So today I wanted to do a blog post on an executable SHA-256: 408e38b4d81de63e5762dcb8024f81360b426429821f9934b087aa0a6b44c56f that has been tied back to the Gamaredon Group, in my research. I pulled it down from @0xffff0800 .onion website http://iec56w4ibovnb4wc.onion/Library/GamaredonGroup/. Thank you @0xffff0800 with sharing these samples with the community!
A little background on who the Gamaredon Group is. According to https://attack.mitre.org/groups/G0047/ and https://unit42.paloaltonetworks.com/unit-42-title-gamaredon-group-toolset-evolution/ the Gamaredon Group is a threat group that has been active since at least 2013 and has targeted individuals likely involved in the Ukrainian government. In the past they relied on more off-the-shelf tools and have made a shift to custom developed malware. Now that we have a little background on the Gamaredon Group let’s begin…
So I will jump straight into the behavioral analysis portion. Some interesting things I was able pull out were, is that it drops a couple of files to disk named ie_cash.cmd and ie_cash.exe that are in a self extracting 7 zip archive.

Now I want to dig into that .cmd file and see what I can determine from it. 
Right away I can see it setting variables for my computername at “EciYJop”, http at “FICvuEG”, bitsadmin at “wtyCwMz”, ddns.net at “per_16” and then it builds the URL in “JhtQFgc”. The next part of the script is setting variables to the dropped and dowloaded executable setup.exe and ie_cash.exe, as well as setting variables to the %APPDATA%\Microsoft \IE directory. It will then copy over ie_cash.exe to that directory. In my behavioral analysis I did not observe this as ie_cash.exe remained in %APPDATA\local\Temp\7ZipSfx directory. The last part of the script is creating two scheduled tasks. So this script was fairly straight forward.
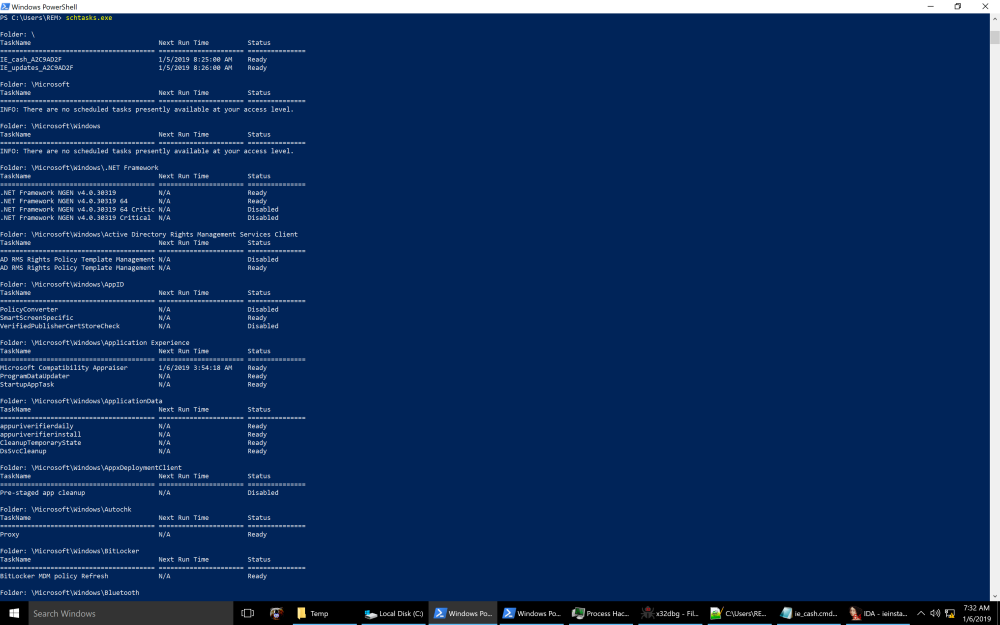
In my debugging of the file it appeared the CreateFileW API was used to create ie_cash.cmd and ie_cash.exe.


Then ShellExecute was used to run ie_cash.cmd which in turn set the scheduled tasks and ran ie_cash.exe. I believe ie_cash.exe to be the downloader for http[://]bitsadmin.ddns[.]net/%COMPUTERNAME%/setup.exe.


I also noticed that the cmd.exe that it starts was started suspended and later NtResumeThread was used to restart it. The handle of the first argument pointed to cmd.exe. This could indicate some sort of injection.

Well thank you for taking time to read my post and until next time…
Happy hunting,
Marcus